Information Management
- Strategy (Stance, Approach, and Awareness of Risk)
- Governance
- Risk Management
- Indicators and Targets
- Major Initiatives
(Stance, Approach, and Awareness of Risk)
Basic Concept
SEKISUI CHEMICAL Group has established systems and operation systems to ensure the confidentiality, integrity, and availability of information systems in order to avoid the occurrence of serious incidents related to information management that could affect the improvement of sustainable management capabilities. At the same time, we are working to improve the IT literacy of our employees through e-learning and incident response training.
We consider the following major incidents related to information management to be risks that could cause corporate value to be impaired.
- 1.Exploitation and destruction of data by cyber attacks
- 2.Large-scale and long-term information system failures
- 3.Leakage of personal information and confidential information, and violation of the Data Protection Law
Cyber Security Policy
The Group has formulated the Cyber Security Policy*for all Group companies. This Policy is publicized both inside and outside the Company. In this way, we are working to strengthen our Group-wide cyber security measures.
- For details of SEKISUI CHEMICAL Group’s Cyber Security Policysee here
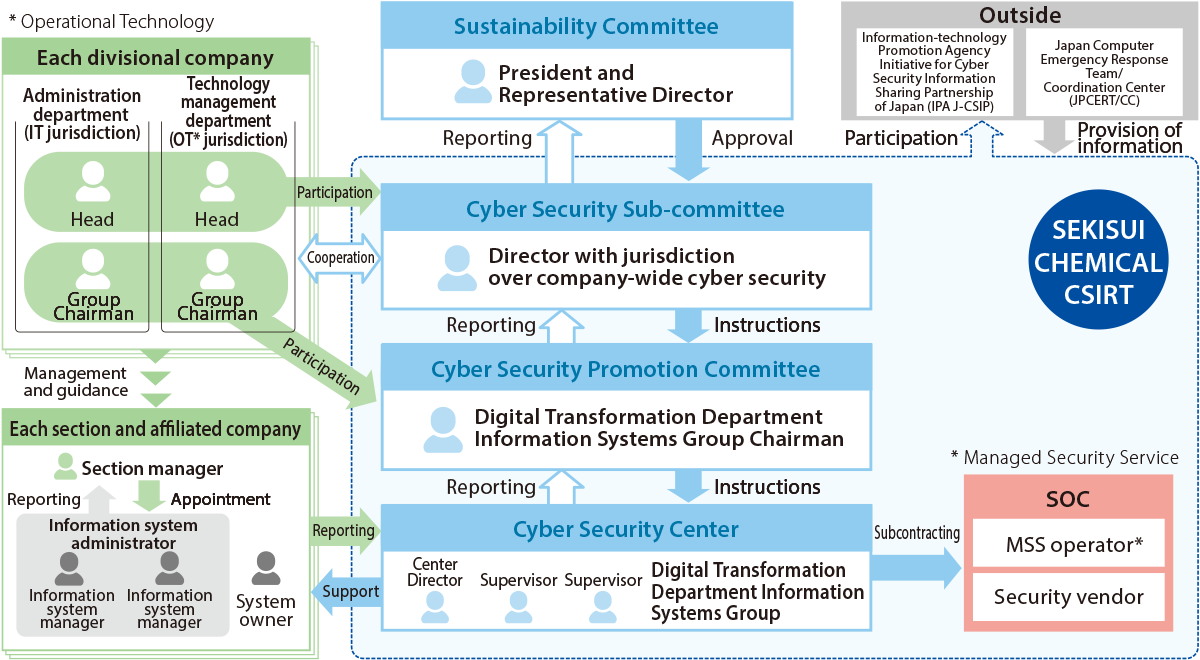
Cyber Management System
SEKISUI CHEMICAL Group has established CSIRT*1 under the Sustainability Committee, which is chaired by SEKISUI CHEMICAL’s president, as an organization for dealing with cyber security.
CSIRT has established the Cyber Security Subcommittee as the policy-making body for information security. The subcommittee is chaired by Tatsuya Nishida, CISO (Chief Information Security Officer), and discusses Group-wide cyber security measures and significant security incidents.
The Cyber Security Promotion Subcommittee is responsible for promoting measures based on decisions made by the subcommittees, and has established the Cyber Security Center as a working unit.
The Cyber Security Center works with SOC*2 to monitor networking and device security. Security monitoring is conducted 24 hours a day, 365 days a year to ensure the early detection and recovery of incidents.
At least one information system manager has been assigned to each site to build an information management system that encompasses the entire Group. Even if there is an organizational change or a change in the information system administrator, the list management system allows us to keep track of the presence or absence of the information system administrator at each office.
In the future, we will upgrade the operation of CSIRT domestically and promote the establishment of CSIRT at overseas Group companies.
- Computer Security Incident Response Team, or CSIRT, is the title given to specialized teams that receive reports, conduct surveys and enact response measures related to computer security incidents at companies and other organizations.
- The Security Operation Center, or SOC, is a specialized entity devoted to monitoring and analyzing threats to information systems. It works to detect threats as soon as possible, and plays a role in supporting the CSIRT with its response and recovery efforts.
- 09-57
Diagram of Overall Management System
SEKISUI CHEMICAL CSIRT's Protection Activities
SEKISUI CHEMICAL CSIRT's activities to protect confidential information, personal information, and information systems are as follows.
Plan: Planning and review
- Planning of cyber security enhancement plans
Do: Implementation of upgrade planning
- Strengthening overseas cyber security measures
- Educational activities for employees using e-learning
- Cyber security of the supply chain and thorough information management
Check: Inspection and assessment
- Report on risk assessment to the Cyber Security Subcommittee and report on countermeasures to the Cyber Security Promotion Subcommittee
Act: Improvement activities
- Setting improvement targets based on the results of activities and revising action plans
Targets
SEKISUI CHEMICAL Group has identified zero cyber security incidents as a KPI under its current Medium-term Management Plan and taken steps to promote information management activities. The purpose is to prevent any damage to its corporate value due to serious incidents.
As a result of these activities, there were no significant cyber security incidents in fiscal 2023. The results of major implementation measures are as follows.
Major Implementation Measures Chart
| Major Implementation Measures | Management Indicators | Final Fiscal Year (FY2025) Targets of the Current Medium-term Management Plan | FY2023 Results |
|---|---|---|---|
| Rapid response to cyber security incidents (Japan) | Detection to recovery time | Within 3 business days | 3 business days |
| Overseas deployment of CSIRT | Overseas CSIRT deployment | Completion of deployment across all regions | Expansion to North America completed |
Measures Against Information Leaks and Risks
SEKISUI CHEMICAL Group takes measures to ensure the safety of customer information, including personal information, and internal information, including confidential information, from both the perspective of systems and personnel measures. SEKISUI CHEMICAL CSIRT's Cyber Security Center plays a central role in swiftly implementing appropriate measures against external threats. Specifically, we are constantly aware of new threats such as newly reported viruses and targeted e-mails, and update the policies of our security products. In addition, we are working to prevent information leaks by educating employees through e-learning and conducting audits.
CSIRT holds regular Cyber Security Subcommittee and Cyber Security Promotion committee meetings. The subcommittee report on the evaluation of risk measures, while the promotion committee reports on the activities of risk countermeasures. In addition, every year, training sessions are held for subcommittee members to examine their ability to make management decisions in the event of an information security accident.
Key System-related Measures
The Group mainly implements the following system measures.
-
1.Important information is kept on the data center server, and the data center is fortified.
-
2.Complete separation of internal, external, and control networks using a firewall.
-
3.A cloud firewall is introduced that is effective even for direct Internet connections (including remote environments).
-
4.Next-generation antivirus on all servers and PCs.
-
5.The above three points 2. to 4. are monitored 24 hours a day, 365 days a year by SOC.
-
6.Mail filters and Web filters are introduced to ensure the safe use of e-mails and the Internet by employees.
-
7.User authentication infrastructure is revamped for both convenience and safety.
Key Personnel Measures
The Group mainly implements the following personnel-related measures.
-
1.Thorough information management by level of importance.
-
2.Strict confidentiality for retirees and newly hired employees.
-
3.Regular e-learning for all employees.
Provision of additional e-learning to employees engaged in key R&D operations. -
4.Desktop training for CSIRT members (confirming contact flows and questioning ability to make management decisions)
Measures Against Natural Disaster Risks
Our core systems are installed in data centers that are earthquake-resistant and seismic-isolated. This makes it possible to continue operations even if social infrastructure is damaged by a natural disaster. In addition, by setting up data centers in multiple locations, we have built a system that will not delay operations even if a particular data center becomes unusable.
In addition, we are working to shorten the lead time to complete restoration of operations by fully duplicating (backing up) our critical business systems.
Protecting Personal Information
The Group handles the individual information of its customers in accordance with our Privacy Policy.
In addition to complying with laws and regulations related to personal information, we have established voluntary rules and systems based on our internal confidential information management regulations to ensure appropriate protection.
In addition, we have established the Guidelines for Web Server Construction and Management to protect the servers that handle personal data management by related companies and departments.
At the same time, management privileges, such as access rights, are restricted according to the importance of handling information to ensure thorough management.
Furthermore, we are strengthening our governance of the handling of individual (customer) information by raising employee awareness and providing education, mainly during the Compliance Reinforcement Month every year.
Preventing Leakage of Technical Information
In addition to measures to prevent leaks using IT technologies, we have introduced risk-management activities to departments that handle confidential technical information. We also provide moral education and training for engineers, and ensure that confidentiality is strictly enforced when hiring.
